Modern Security Operations Centers (SOCs) are drowning in an overwhelming volume of time-sensitive threat reports and alerts. Enterprise SOCs commonly face upwards of 10,000+ security alerts per day, coming from IDS/IPS, SIEM, EDR, cloud logs, threat intel feeds, and more. In fact, 90% of SOCs report being overwhelmed by alert backlogs and false positives, with 66% of teams unable to keep pace with the incoming alerts. This deluge creates a scenario where critical signals are buried in noise, and analysts struggle to triage everything in real-time. Adding to the pressure, many threat intelligence reports – such as vulnerability disclosures or threat actor TTP updates – are extremely time-sensitive. For example, nearly one-third of recently disclosed vulnerabilities were exploited by attackers within 24 hours of public disclosure.
This means SOC teams have mere hours (or less) to interpret new threat reports, identify relevant Indicators of Compromise (IOCs), and take action before threat actors strike. The combination of high volume and urgent turnaround stretches traditional SOC workflows to their limits, contributing to alert fatigue, burnout, and an increased risk of missed threats.
Amid these challenges, AI in threat intelligence has emerged as a game-changer. Anthropic’s Claude AI – a large language model (LLM) tuned for complex reasoning – offers a powerful AI threat analysis tool that can read and analyze threat reports at machine speed, potentially outpacing even large SOC teams. In this article, we’ll explore how Claude AI accelerates the threat intel lifecycle, from ingesting unstructured reports and extracting IOCs to mapping threats onto frameworks and recommending responses. We’ll also examine the limitations of traditional SOC triage (alert fatigue, manual correlation, lack of context) and show how SOC automation with Claude helps overcome these issues. Real-world use cases will illustrate how Claude can accelerate threat triage – for instance, condensing 20 related alerts into 1 actionable incident or correlating anomalies across cloud logs. The goal is to demonstrate why a solution like Claude AI can drastically reduce Mean Time to Triage (MTTT) and Mean Time to Detect (MTTD), allowing enterprise security teams to respond faster than ever before.
The Alert Fatigue Epidemic in SOCs
High alert volumes have led to an epidemic of alert fatigue in SOCs. Analysts start each day facing a torrent of SIEM notifications, threat intel feeds, and security product alerts – far more than any human team can reliably handle. Studies show a staggering 62% of alerts are ignored entirely by SOC analysts due to overload. A typical enterprise might get thousands of alerts per day and simply cannot investigate them all; one survey found an average of 3,832 alerts per day per SOC, of which a large portion are never addressed. This constant barrage desensitizes analysts: they become prone to missing genuine threats amidst the noise. Over time, teams experience decreased accuracy, slower responses, and burnout as they try to keep up.
Traditional SOC triage workflows have critical limitations:
- Manual, Siloed Alert Handling: Analysts must pivot between disparate tools (SIEM, EDR consoles, threat intel platforms) and manually correlate data points. For example, an analyst might see an IDS alert for a malicious IP, then separately check threat intel reports for that IP, and then query firewall logs – performing all correlations mentally. This manual cross-referencing is slow and error-prone. With dozens of security tools generating isolated alerts, there’s often no unified view, forcing analysts to piece together the puzzle by hand.
- Lack of Context and Prioritization: Most alerting systems provide minimal context – a raw indicator or rule trigger – with little insight into relevance or severity. All alerts tend to appear equally urgent, causing teams to treat benign and critical events with the same initial priority. There is typically no built-in risk-based scoring; an alert about a malware download on a low-value kiosk gets as much attention as one about suspicious admin activity on a critical server. This lack of contextual prioritization wastes precious time on low-risk events while truly dire threats might be overlooked. As Palo Alto Networks notes, without understanding an alert’s severity, affected asset criticality, or threat intel context, analysts are essentially flying blind on what to tackle first.
- Alert Overload and False Positives: Poorly tuned detection rules and sensitive scanners produce countless false positives. Studies estimate 83% of daily alerts are false alarms or low-value informational notes that do not require action. After reviewing hundreds of such noisy alerts, analysts become numb (“cry wolf” effect) and may start ignoring even legitimate warnings. Multiple surveys show analyst accuracy drops significantly after just a few hours into a shift, as the cognitive load erodes their focus. The net effect is an environment where real threats can slip through – for example, 13% of security incidents in a 2025 study were traced back to alerts that were ignored or untriaged due to overload.
The consequences of these limitations are severe. Organizations face increased breach risk because critical alerts are missed or delayed. One overlooked alert can mean a foothold for attackers, leading to a major incident. Meanwhile, Mean Time to Detect (MTTD) grows longer as threats dwell unnoticed. Human fatigue also means slower investigation of those alerts that are picked up, inflating the Mean Time to Triage (MTTT) each incident. Simply hiring more analysts is not a complete solution – the complexity and speed of modern attacks demand smarter, more automated approaches. This is where Claude AI comes into play, offering a way to intelligently automate triage and enrich alerts with context so that human analysts can finally break out of the fatigue cycle.
How Claude AI Accelerates the Threat Intelligence Lifecycle
Claude AI, Anthropic’s advanced LLM, is designed to ingest and analyze unstructured data with human-like comprehension. In the context of threat intelligence and SOC operations, Claude can dramatically speed up each phase of the threat lifecycle. Here’s how Claude AI cybersecurity workflows improve upon traditional methods:
1. Parsing Unstructured Threat Reports at Machine Speed: SOC teams regularly receive unstructured reports – vendor threat bulletins, security blogs, CVE disclosures, incident reports, etc. – which can be pages of technical text. Claude reads and understands these natural-language documents in seconds, a task that might take an analyst hours to carefully parse. The model can summarize lengthy threat reports and CVE advisories, extracting key details such as the threat actor’s tactics, impacted systems, and recommended mitigations. For example, researchers have demonstrated pipelines where an LLM first generates a concise summary of an attack scenario from a verbose report. Claude’s natural language processing is fluent in cybersecurity jargon, so it can digest a FireEye APT report or Microsoft threat intel blog and immediately highlight the most important points for the organization.
2. Automated IOC Extraction with Context: A crucial part of threat analysis is identifying indicators of compromise (IOCs) – IP addresses, domains, file hashes, email addresses, etc. – that signal malicious activity. Claude AI excels at pulling IOCs out of dense text while preserving the context around them. This contextual understanding is key; as studies note, “IoCs like IPs and URLs are often buried in reports that lack consistent formatting…identifying them accurately requires understanding context that may be scattered in the document.”. Simple regex-based tools often either miss IOCs or flag benign strings as malicious because they have no contextual awareness. Claude, however, can interpret sentences to discern whether “mail.evilcorp.com” is the attacker’s C2 server or just mentioned in passing. It can extract IOCs and label their significance (e.g. “this IP is the threat actor’s exfiltration server in the campaign”). By doing so, Claude reduces the manual toil of IOC hunting. It also means fewer false positives – the AI is less likely to tag an innocuous domain as malicious because it “knows” via context whether it’s part of the attack narrative or not. In one human-in-the-loop test, an LLM-based system provided explainable IOC labels to analysts and cut verification time by 43%, combining speed with accuracy. This kind of rapid IOC extraction and triage would allow a SOC to, say, ingest a new threat report about a phishing campaign and within seconds have a list of malicious domains/IPs from the report ready to cross-check against their network logs.
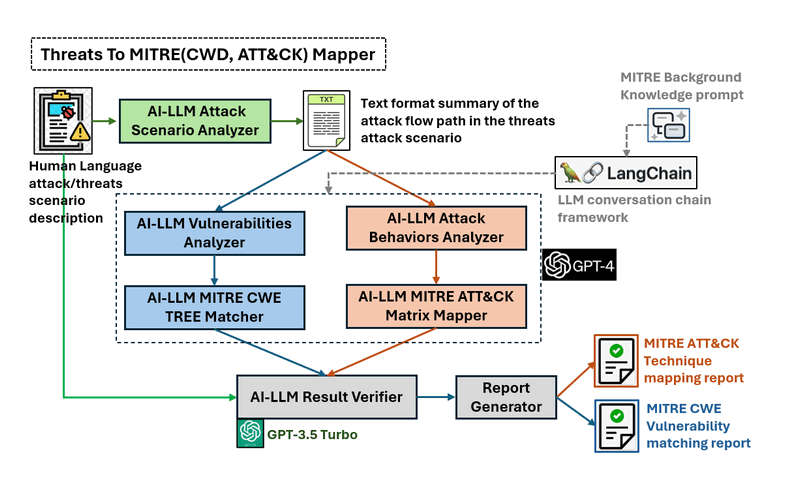
3. Mapping Threats to MITRE ATT&CK (and Other Frameworks): One of the more tedious tasks for analysts is translating a threat report into standardized tactics, techniques, and procedures (TTPs). Claude can automate this mapping by reading the attack description and linking each adversary behavior to the MITRE ATT&CK framework. For instance, if a report says “the malware established persistence by creating a scheduled task,” Claude will recognize this as Technique T1053 – Scheduled Task under the Persistence tactic. It performs this by identifying each attack behavior in text and mapping it to the corresponding ATT&CK tactics/techniques. It can similarly map any mentioned vulnerabilities to the MITRE CWE (Common Weakness Enumeration) category. The end result is an AI-generated mapping report that outlines the entire attack flow in ATT&CK terms. Security teams benefit by quickly seeing which tactics/techniques are in play, making it easier to correlate with defenses or logging (e.g. “Technique X was used – do we have detections for that?”). This also helps in understanding the adversary’s likely progression. Claude essentially serves as an assistant that performs the tedious ATT&CK mapping in seconds, a task that could take a human analyst a significant amount of time and ATT&CK expertise.
4. Risk-Based Alert Prioritization and Enrichment: Not all threats are created equal for a given organization. Claude AI can intelligently rank threats by severity and relevance to your environment – something traditional tools rarely do automatically. It achieves this by combining contextual data: the content of the threat report, knowledge of the organization’s assets, and even real-time log data. For example, if a new CVE report comes in, Claude can note the CVSS score (say 9.8 critical) and check if that software is present in your asset inventory. A critical vulnerability that exists in your environment would be ranked high priority, whereas a medium-severity issue affecting, say, only macOS when you run no Macs might be ranked lower. Additionally, Claude can correlate IOCs from threat intel with internal telemetry – if an IOC from a high-profile threat report was observed in your SIEM logs, that incident gets escalated in priority. This context-driven scoring is the kind of risk-based prioritization experts have long called for. By assigning a dynamic risk score (factoring threat severity, asset criticality, exploit likelihood, etc.), Claude ensures that analysts focus on truly urgent threats first. This prevents the situation where trivial or irrelevant alerts consume as much time as critical ones, thereby improving the signal-to-noise ratio. In essence, Claude provides the “big picture” context that a human analyst would assemble (given enough time), but does it instantly. Security teams can go from reacting to every ping blindly to responding based on clear risk prioritization.
5. Suggesting Response Playbooks and Mitigations: Going beyond analysis, Claude can also assist with the response phase by recommending remediation steps and playbook actions. After analyzing a threat or incident, the AI can suggest a tailored checklist of actions for containment and recovery. For instance, if the threat report is about a new ransomware strain, Claude might recommend steps like “isolate affected host from network, initiate backup restoration procedures, update EDR signatures, and notify legal/PR if data breach is suspected.” These suggestions can be drawn from known best practices, the organization’s own runbooks, or relevant compliance requirements. In cases of a phishing campaign, Claude might suggest “reset passwords of targeted users, search email logs for all instances of the malicious link, and push an MFA challenge to any suspicious login.” By having an AI generate an initial response plan, SOC teams save time drafting remediation steps and ensure no critical action is overlooked. These recommendations can integrate with Security Orchestration, Automation, and Response (SOAR) tools – effectively, Claude can act as the brains that triggers automated playbook actions. Industry approaches already hint at this synergy: SOAR platforms use standardized playbooks that allow one-click or fully automated responses to common threats. Claude takes it a step further by dynamically writing or selecting the appropriate playbook based on the unique context of the incident. This bridges the gap between detection and response. The end result is faster containment (reducing Mean Time to Respond, MTTR) and a more consistent, thorough response process guided by AI. Human responders remain in the loop for high-level decisions, but Claude handles the heavy lifting of figuring out “What should we do next?” in an incident.
Claude’s Key Capabilities Under the Hood
Claude’s effectiveness in accelerating threat analysis stems from several technical capabilities that differentiate it from traditional rule-based systems. Understanding these features can help enterprises see how Claude integrates into SOC workflows:
- Natural Language Mastery Across Sources: Claude is built to understand human language with near-expert comprehension. It can ingest data from multiple sources – e.g. an MITRE ATT&CK technique description, a Splunk log entry, a CrowdStrike threat report, and an internal wiki page – and make sense of them holistically. This is far beyond keyword matching; Claude actually “reads” and interprets the meaning. For security teams, this means previously untapped data (like lengthy analyst notes or free-text audit logs) can be leveraged in analysis. Claude’s powerful NLP capabilities allow it to perform tasks like entity recognition (finding all IPs, user names, file paths mentioned), summarization, translation (turning pseudo-code or hex dumps into explanations), and more. It essentially serves as a universal parser for security data, breaking down silos between different data formats and sources.
- Anomaly Detection and Pattern Recognition in Logs: While not a SIEM or ML anomaly detector per se, Claude can still contribute to finding needles in the haystack of logs. Given logs or events as input (in plain text or JSON), Claude can identify patterns and outliers by drawing on its training and reasoning. For example, feed Claude a sequence of authentication logs and it might flag that “several failed login attempts were followed by a success for user X from a new IP, which is unusual”. Unlike traditional algorithms that require predefined thresholds, Claude can apply reasoning to see if a sequence of events “tells a story” of an attack. It can correlate an email log with a firewall log by understanding that an email attachment hash appearing in network traffic is suspicious. Claude’s knowledge base (up to its training cutoff and supplemented via prompt) includes many known attack patterns, so it can recognize techniques like port scanning behavior, data exfiltration bursts, lateral movement, etc., even across different log types. In essence, Claude brings a form of human-like intuition to log analysis – something very powerful when coupled with the speed of automation. This can dramatically reduce false positives (by adding context to raw events) and catch complex combined patterns that single-point analytics would miss. Indeed, leveraging AI-driven analytics can “identify anomalous activities that deviate from baselines, often indicating genuine threats with fewer false positives”.
- API Integration with SOC Tools (SIEM, EDR, Ticketing): Claude AI can be integrated via APIs into the existing SOC toolset, acting as a smart assistant woven into workflows. For example, Claude can integrate with a SIEM: when an alert triggers, the SIEM can pass the event details and related log snippets to Claude for analysis. Claude might enrich that alert by querying an EDR API for host details (via a connector) or pulling threat intel context (via an OpenAPI integration). The results – say, an English summary of the incident with ATT&CK mapping and recommended actions – can then be fed into the case management system (JIRA, ServiceNow, etc.) for the analysts to review. This kind of end-to-end integration is already being implemented. In eSentire’s AI-enhanced SOC, Claude was orchestrated through AWS Lambda and Amazon Bedrock to perform dynamic investigations, with secure API gateways controlling access to data and actions. Claude could automatically execute queries (via API calls) and even take containment actions through scripted automations. For a typical enterprise, this means Claude can sit on top of your security stack and act on data in real time. It can retrieve relevant info on-demand (e.g. “pull all logs for this IP from the past 7 days” or “check VT for this file hash”), saving analysts from manually running those searches. And when an analysis is complete, Claude can log the results in your ticketing system with full evidence and reasoning for auditability. This tight integration transforms Claude from a standalone AI into a seamless co-pilot within the SOC, amplifying the capabilities of all your existing tools through intelligent automation.
- Continuous Learning and Adaptation: While not sentient, Claude can be continually refined and adapted to your organization’s needs. Analysts can provide feedback on Claude’s outputs (correcting an interpretation, adding context about internal systems), and these can be used to tune prompts or even fine-tune private versions of the model. Over time, Claude can accumulate knowledge about the organization’s environment – such as common network segments, key executives to watch (for spearphishing), typical user behavior baselines – which further enhances its accuracy. Unlike static playbooks, Claude’s knowledge base can be updated with the latest threat intelligence daily. It can be prompted with new IoCs or vulnerability data as they emerge, ensuring it stays current with the threat landscape. In practice, this means Claude’s recommendations and detections get smarter and more customized the more you use it. SOC teams benefit from an AI that learns their environment’s “normal” and the threat intel most relevant to them. This continuous improvement loop helps maintain effectiveness even as threats evolve.
Reducing MTTT and MTTD with AI-Powered Triage
Two crucial metrics in security operations are Mean Time to Triage (MTTT) – the average time it takes to assess and categorize an alert – and Mean Time to Detect (MTTD) – the time it takes to detect a threat in the environment (often measured from intrusion to detection). By deploying Claude AI in the SOC, organizations can significantly shrink both MTTT and MTTD, leading to faster containment and less damage from attacks.
Faster Alert Triage (Lower MTTT): Traditionally, when a new alert comes in, a Level 1 analyst might spend 15-30 minutes gathering data: querying threat intel sources, pulling related logs, checking asset information, etc., before deciding if the alert is a true incident or a false positive. With Claude handling the heavy lifting, this triage cycle can be cut to seconds. The AI instantly enriches the alert with context (related events, threat intel matches, severity assessment) and often can provide a recommendation (“escalate to incident” or “likely benign, no action needed”). Analysts no longer need to manually research each alert one by one. As a result, the average time to triage an alert plummets. One AI SOC platform example noted that analysts manually have to pull intelligence from multiple sources and correlate alerts, leading to delays, whereas AI agents can autonomously gather data from SIEM, EDR, identity logs, etc., correlate it, and present a structured summary for triage. This means instead of, say, 20–30 minutes per alert, an analyst might only spend 1–2 minutes reviewing the AI’s findings and making a decision. The overall triage capacity of the SOC grows exponentially – the team can handle many more alerts per hour without overwhelm.
Real-world results bear this out. In a case study with eSentire (a Managed Detection and Response provider), incorporating Claude AI led to “hours of expert investigation depth delivered in just minutes”, effectively compressing what used to take a human days or weeks of analysis into near-real-time outcomes. With Claude validating and investigating alerts, eSentire achieved 95% alignment between the AI’s conclusions and their senior analysts’ conclusions in testing, meaning the AI triage quality was on par with human experts. In practical terms, this boosted the threat analysis validation rate to 90% and allowed eSentire to stop 99.3% of attacks on the first compromised machine. Stopping an attack at the first machine indicates incredibly fast detection and response – the lateral spread was prevented because the AI-guided investigation caught it almost immediately. Clearly, Claude can slash MTTT by automating initial investigations and letting humans intervene only when needed, resulting in far quicker escalation of real incidents.
Quicker Threat Detection (Lower MTTD): Mean Time to Detect is often a factor of how quickly subtle attack signals can be pieced together. Humans might take days to notice that an odd pattern in web server logs correlates with a slight increase in failed logins on a database – clues that together indicate an ongoing intrusion. Claude can recognize these patterns and correlations much faster, often in real-time as data streams in. By continuously analyzing activity (or on-demand when prompted by an alert), the AI might surface a likely incident hours or days before a human analyst would connect the dots. This proactive synthesis of weak signals means threats are detected earlier in the kill chain. The earlier you detect, the less damage done – for instance, catching ransomware during the initial encryption attempts vs after it has spread to hundreds of systems.
Furthermore, because Claude can handle the flood of low-level alerts by bundling them into high-fidelity incidents (e.g., grouping 50 related alerts into 1 incident), it ensures that nothing truly malicious goes ignored. As mentioned earlier, modern AI-driven SOC platforms aim to present “a single, correlated incident instead of a thousand individual alerts for a campaign”. Claude embodies this approach – by correlating multiple weak alerts into one strong story, it guarantees the malicious activity is recognized as such, rather than dismissed as noise. This directly reduces MTTD because the clock to detection starts when those minor alerts fire; if they’re never pieced together, detection is effectively “missed.” Claude removes that chance. According to the 2025 Verizon DBIR, the median dwell time (time an attacker lurks before detection) was 11 days, which is already an improvement historically. With AI like Claude, we can drive dwell times even lower by spotting intrusions within minutes or hours of initial compromise. Early containment means an intrusion might be just a minor incident, not a business-crippling breach.
In summary, Claude accelerates both the triage of alerts and the overall detection of incidents. By reducing MTTT, analysts have more time to focus on real attacks (and on proactive hunting and hardening, rather than shuffling through alerts). By reducing MTTD, organizations shrink the window in which attackers can operate undetected, greatly limiting potential damage. These improvements translate directly to a stronger security posture and ROI: faster detection and triage means fewer costly breaches, less downtime, and more efficient use of security staff. The combination of speed and intelligence that Claude AI brings is helping transform SOCs from reactive and overwhelmed to proactive and effective.
Claude AI in Action: Use Case Examples
To make these benefits more concrete, let’s walk through a few realistic use cases where Claude AI could assist a SOC. These examples illustrate how Claude automates and augments tasks that traditionally eat up analysts’ time:
Condensing 20 Alerts into 1 Actionable Incident:
Imagine a malware outbreak scenario: an infected host triggers a dozen different alerts (antivirus, EDR suspicious behavior, abnormal outbound traffic, etc.), and related IoCs are spotted on multiple other devices. A traditional SOC might see a queue of 20 separate alerts and treat them piecemeal, possibly not realizing they are all part of one attack campaign until much later. Claude would immediately parse all incoming alerts and logs, recognize the common thread (e.g. the same malware hash or C2 IP appearing across systems), and correlate these into a single incident summary. It might produce a report: “20 alerts consolidated into Incident #123: Likely Emotet infection spreading – initial vector was phishing email, now lateral movement via SMB, C2 traffic to 203.0.113[.]5.” This correlated incident includes all relevant artifacts and context, saving the analyst from investigating 20 items separately.
As noted earlier, modern approaches favor this incident-centric view – “instead of a thousand alerts, a single, high-fidelity incident with all necessary context”. Claude enables exactly that. The analyst can now address one incident with full understanding, rather than chase many fragmented alerts. This dramatically improves triage efficiency and ensures nothing slips through cracks (since the AI already connected the dots). It also makes reporting and tracking easier – one ticket to update instead of twenty.
Cross-Correlating Cloud Log Data Across Services:
Today’s organizations use a mix of cloud services (AWS, Azure, GCP, SaaS apps), each with its own logging format and portal. Sophisticated threats often span multiple cloud services, making detection hard. For instance, an attacker might steal credentials and login to O365, then from that foothold pivot to AWS resources. A human analyst might not easily link an Azure AD log anomaly with an AWS CloudTrail event hours later. Claude, however, can consume logs from diverse cloud sources and identify related patterns. It could notice that the same IP address that triggered failed logins in Azure AD also accessed an unusual S3 bucket in AWS within the same timeframe – a correlation a siloed tool would miss.
By using natural language understanding, Claude doesn’t mind that one log is JSON and another is CSV or that fields have different names; it interprets their meaning. In a use case, you could ask Claude in plain English: “Find any connections between recent Azure AD alerts and AWS activity”, and it might respond with: “Both Azure and AWS logs show activity from IP 198.51.100[.]77; this IP performed a privilege escalation in Azure AD and then accessed AWS resources under user JohnDoe’s credentials.” This kind of multi-platform correlation effectively gives you a unified view of an attack that traverses cloud boundaries. It accelerates detection of multi-stage, multi-cloud attacks that are notoriously challenging for SOCs. By automating this with Claude, the SOC team can stay on top of complex scenarios without manually stitching together logs from different consoles.
Validating Phishing Campaign Indicators:
Phishing is a constant threat, and when a new phishing campaign hits, organizations receive intel on domains, email subjects, sender addresses, etc. Suppose your threat intel feed shares indicators for an ongoing phishing campaign targeting financial companies. Claude can rapidly validate and contextualize these phishing IOCs against your environment. For example, feed Claude the list of suspicious domains and email senders from the intel report. It can cross-reference these with your email server logs or cloud email API: “The domain badlink.cn from the report was found in 14 emails to our employees over the past week, and 3 users clicked the link – these users should be investigated.” Claude can also parse the phishing email content provided in the report (perhaps as an example phishing lure) and then search through a repository of email logs or tickets to see if similar language or attachments were observed internally.
Essentially, Claude can automate the threat intel consumption process – taking those external reports and immediately telling you “are we affected or not.” This significantly cuts down the time to respond to new phishing threats. Instead of each analyst manually checking a domain or looking through email gateways, the AI does it and produces a concise summary. Additionally, Claude can suggest mitigations specific to phishing: “Recommendation: alert users X, Y, Z who clicked the link to change their passwords; add badlink.cn and associated IPs to blocklists; use provided email subject keywords to hunt for more attempts.” The entire cycle from intel receipt to validation to action can be compressed to minutes with Claude’s help, reducing the likelihood that the phishing campaign succeeds against your company.
Rapid Vulnerability Report Analysis and Patch Guidance:
As another scenario, consider the flood of CVE disclosures and vendor patch releases. A critical vulnerability in a widely used software (say, a VPN appliance) drops with a detailed technical advisory. Claude can read the CVE advisory and vendor threat report the moment they are published and generate an executive summary plus a technical analysis for your team. It would highlight: affected systems (e.g. specific OS or appliance versions), the nature of the flaw (e.g. RCE, privilege escalation), any known exploitation in the wild, and the recommended fix (patch or workaround). Crucially, Claude can also cross-check your asset inventory to list which of your systems are running the vulnerable software version. This turns what is often a frantic scramble – determining exposure and impact – into an instant report.
The SOC could get a message like: “CVE-2025-1234 is a critical RCE in FortiGate firewalls. You have 12 FortiGate instances, 10 are already on fixed version, 2 need patching (hostnames FG-Branch1 and FG-Branch2). Exploit code is expected within 24 hours given historical trends. Prioritize patching those 2 immediately and consider interim IPS rules.” By letting Claude handle the heavy lifting of vulnerability analysis and mapping to your environment, you accelerate remediation and reduce your exposure window. This is especially vital as studies show a significant portion of exploits appear within a day of disclosure – there’s no time to waste. Claude acting as a vulnerability analyst ensures you don’t fall behind in the patch race.
These examples only scratch the surface. From summarizing 20 alerts into one incident, to correlating cross-domain events, to validating intel and automating hunts, Claude AI proves to be a versatile force multiplier for SOC teams. It tackles the grunt work of analysis at machine speed, enabling analysts to focus on decision-making and response. The outcome is a smarter, leaner SOC that can outpace threats rather than drowning in them.
Conclusion: Augmenting the SOC with AI Speed and Intelligence
The challenges facing modern SOCs – alert fatigue, overwhelming threat intel, and increasingly fast-moving attacks – require more than just hiring extra analysts or adding another dashboard. They call for a fundamental boost in the speed, scale, and intelligence with which we analyze security data. Claude AI offers that boost. By combining natural language understanding with integrated reasoning across data sources, Claude can analyze threat reports and alerts faster than humanly possible, while maintaining a high level of accuracy and context. This doesn’t replace human analysts; instead, it augments the SOC team, taking care of the repetitive and time-consuming tasks and surfacing the insights that truly need human judgment.
Enterprise security teams adopting Claude AI have reported more consistent and deeper analyses delivered in a fraction of the time. Alert floods that once led to analyst burnout can now be triaged through AI, with only the truly significant incidents escalating for human response. The end result is a dramatic reduction in missed threats and faster containment of those that do arise. Key SOC metrics like MTTD, MTTT, and MTTR all improve when an AI co-pilot like Claude is embedded in the workflow. Perhaps most importantly, analysts can finally spend more time being proactive – hunting for threats and improving defenses – rather than reacting to every blinking alert. AI-driven context and prioritization means the team’s limited attention is always focused on the highest-risk issues.
In the ever-evolving cat-and-mouse game of cybersecurity, speed and knowledge are everything. Attackers are already leveraging automation and even AI to launch attacks at scale. It’s only fitting that defenders arm themselves with advanced AI assistants. Claude AI exemplifies how SOC automation with AI can tip the scales back in favor of the defense – digesting threat intelligence in real-time, learning an organization’s network on the fly, and responding at machine speed. By embracing tools like Claude, organizations can transform their SOCs into agile, intelligent, and resilient operations that mitigate threats faster than adversaries can exploit them. The synergy of human expertise and AI’s computational power is the key to staying ahead of modern cyber threats, and Claude AI is helping leading security teams achieve that today.